


Please note that I don't really do much in the way of updates very often. I don't know why you bother coming here.
Greg looks all right in a suit, and has even been a magazine cover model! Of course, Greg got older. This is a 2007 professional photo.
![]()
Early morning of 11/9 was the culmination of a major terrorist attack. Women in the US and around the world woke up that morning in fear, that they will be groped in the elevator, denied advancement because of their looks, and unable to make their own decisions about their bodies.
In 1967* (before Roe.v.Wade, but at a time when some states allowed abortion but others did not) about 200 US women per year died because of complications to illegal abortions. If safe, legal abortion is outlawed in the US, given the population increase since 1967, it is not at all unlikely that 300 or more fatalities per year will be caused by botched illegal abortions. In ten years, the total death toll could exceed that of the 9/11 attacks. More than half of the population would be affected by such a change.
Of course other minorities are also terrorized by the 11/9 outcome. Undocumented immigrants woke to the fear that they might have their families broken up or be deported back to a country where their lives would be at serious risk. Muslims woke to the fear that they will be attacked in random acts of violence (several such attacks have happened in the subsequent week), or be hindered in the exercise of their religion. Black people fear that they will be killed by police in traffic stops with no justice available to their families. Everyone should fear that many deaths will be caused by coal and oil pollution.
Women are the hardest hit by 11/9. Please support Planned Parenthood. If you don't care about women, but you're not a privileged white male, you could always support the American Civil Liberties Union .
* See the 2003 Guttmacher Institute report: Lessons from Before Roe: Will Past be Prologue?
Well, I was looking up something else on my own web site, and realized that this needed to be updated. The reality of the Trump soi-disant administration embodies all of the above, and more.
But I wanted to add one data point. Well, a couple really. Even before the new regime, TRAP (Targeted Restrictions on Abortion Providers) legislation in many US states had already had the undesirable effects on womens' health mentioned above. For example: deaths doubled in Texas (and this includes deaths unrelated to actual abortions), or Maternal deaths fall across globe but rise in US, doubling in Texas
![]()
Some interesting cryptographic utilities and papers can be found at QUALCOMM's open source portal. (These used to be at qualcomm.com.au. Moved to corporate then disappeared. The link is now to archive.org (the wayback machine))
Greg uses cryptography extensively, and has some interesting links. His various PGP public keys are available (if you can't use the newer style Diffie-Hellman/DSS keys you need this instead). Note that Greg uses a multi-level key scheme, with a very secure top level key and less secure keys for personal/USENIX and QUALCOMM related work. Or you can use S/MIME encryption with this CAcert certificate. Secure voice / text: Seecrypt greg.rose@seecrypt.com (this is as close as you'll get to a phone number on this web page).
He also developed the PGP Moose which allows newsgroup moderators to authenticate postings, and which automatically cancels unauthentic postings. This is still in use but not really supported any more.
Greg was the Program Chair for USENIX's Sixth USENIX Security Symposium focusing on Applications of Cryptography and was invited talks coordinator for the 7th USENIX Security Symposium For the Eigth, he was Works-In-Progress coordinator. For the Ninth, he was Program Co-Chair with Steve Bellovin. Tenth, Invited talks coordinator again. Taking a rest. He worked on a PGP key signing service and electronic voting for USENIX.
Greg was a member of the Board of the
International Association for Cryptologic Research, by virtue of having served
as General Chair of
Crypto'03.
He served as treasurer 2011-2016,
re-elected as vice president (president of vice)
on the board again 2017-2020.

Greg developed the SOBER family (including Turing, NLS, Shannon and Boole) of stream ciphers for embedded application. This and other software and publications can be found at QUALCOMM's open source portal.
Greg is proud to be founding life member #1 of LOPSA, the League of Professional System Administrators, for which he was also on the leadership committee. As of 2025-06-17, LOPSA has been dissolved.
Greg for a while became President of CAcert, Inc, a not-for-profit Certificate Authority that issues free certificates based on a web-of-trust identification model.
Greg is the lesser co-author of
BigNum Math
 with
Tom St Denis.
with
Tom St Denis.
Greg supports the American Civil Liberties Union of San Diego and Imperial Counties
 ,
,
The Southern Poverty Law Center 
and
Planned Parenthood of the Pacific Southwest  .
.
Greg is currently on the board of the American Constitution Society, a not-for-profit that helps lawyers progress toward bench positions.
![]()
Founder and Managing Director of Fawnray Pty Ltd (became Neology Ltd). Founder and Managing Director of Softway Pty Ltd, became AUREMA, sold to Citrix in 2006, long after Greg left. Visiting Scientist at IBM's Thomas J. Watson Research Center in 1991. Manager of the Open Distributed Systems Program at the Australian Computing and Communications Institute. UNIX product engineer for Sterling Software. Joined QUALCOMM in July 1996 as a senior staff engineer/manager, working on cryptography and authentication for CDMA cellular phone systems, and to set up the office of QUALCOMM Australia. Moved to the USA in 2004. Was senior vice president of engineering, in the office of the chief scientist, with responsibility for day to day management of up to 230 researchers.
In January 2014, left Qualcomm to refresh technical skills in security and cryptography, and devote more time to extracurricular activities such as not-for-profit organizations.
Greg was CEO of Allocrypt, Inc, "Bringing security to diagnostic devices".
Greg is Chief Scientist and a founder of Deckard technologies, Inc, "Transforming real estate data into actionable insights, helping local governments enforce regulations with equity and fairness."
Involved with the use and development of the UNIX Operating System since its arrival in Australia in 1974. Founding secretary and past president of AUUG. Founding treasurer of SAGE-AU, the System Administrator's Guild of Australia. Past Vice President of the USENIX Association. Past Member of the Board of Directors and past Vice President of the International Association for Cryptologic Research. Past President of CAcert, a free certificate authority.
Experienced teacher at university and in private courses, mostly involving cryptography and security, programming languages, operating systems, and implications of software and hardware technology.
![]()
Greg has a surprising (to him) number of patents.
I used to have direct links to queries that would return lists of patents, but unfortunately the USPTO has deprecated that functionality. Instead, go to https://ppubs.uspto.gov/pubwebapp/static/pages/ppubsbasic.html for a basic search, and fill in the desired Assignee:
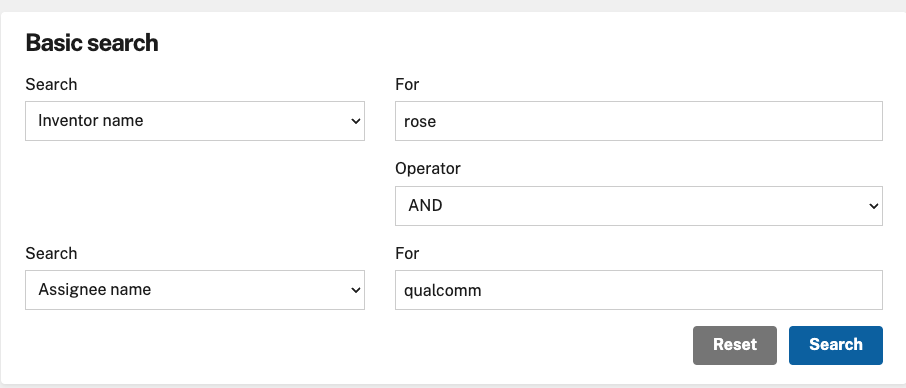
At the time of writing (late 2023), you have a choice of Assignees:
Qualcomm, 147 patents
Targetproof, 2 patents
Deckard, 3 patents.
![]()
Many years ago now (2001, last minor revision in 2004), I wrote a full day tutorial called "Cryptographic Algorithms Revealed". Here are the slides and printable notes pages. This is the original blurb for the course:
This tutorial will require some mathematical background from
attendees. At the very least, familiarity with common mathematical
notation, polynomials, and some elementary statistical knowledge will
be needed. You've been warned.
In this advanced tutorial, attendees will get a fairly detailed overview
of what makes cryptographic algorithms work, and when they don't work,
how they are broken. Some of the AES finalists are covered to provide
lessons in block ciphers, with the winner (Rijndael) treated in depth.
Topics covered (unless time runs out):
Brief History
substitution and transposition
development of DES
public key cryptography
Symmetric Block Ciphers
Feistel ciphers generally
DES
Other AES Candidates (Twofish, RC6, Serpent)
Rijndael (AES) in depth
Block Cipher modes of operation
Symmetric Stream Ciphers
Linear Feedback Shift Registers
A5, SOBER and other LFSR based constructions
Cryptanalysis
Differential & Linear cryptanalysis
Attack assumptions and threat models
Attacks on stream ciphers
Public Key systems
Group and Finite field theory
Discrete Log systems (El Gamal, Diffie-Hellman, DSS)
RSA
Elliptic curves
Other stuff:
Hash functions, SHA-1, SHA-256
Recently, people have been asking me for some of my old publications
(generally not crypto related). Many of them are in archaic formats. When I get
a round tuit, I might put more of them here. For the moment, here is:
I wrote a paper KISS: A Bit Too Simple published in the journal Cryptography and Communications. Here are the corresponding presentation slides.
I was (Oct 2011) keynote speaker at the CIPHERTEC WORKSHOP on the THEORY and APPLICATIONS of CRYPTOGRAPHY in Pretoria, South Africa (not my capitalization!). Here are the slides from my talk about stream ciphers.
![]()
This web page was carefully handwritten by me, using archaic tools like vi. If you have comments, please send them to ggr@seer-grog.net
Greg Rose (ggr@seer-grog.net)